Blog
Stay Compliant: Understanding FDA's Cybersecurity Guidelines for MedTech Firms
Medical devices have evolved and come a long way, transitioning from standalone to cloud-connected systems. These devices, from radiology equipment to wearables and implantable devices, have better interconnectivity and software components, which can help deliver better patient care.
Also, their widespread adoption in clinical and even home practices has led to better patient experience, care delivery, monitoring, and overall clinical outcomes. However, the increase in connectivity has made these devices susceptible to cybersecurity issues in medical devices and privacy breaches.
Why CyberSecurity is Important in Healthcare?
The healthcare industry is the most targeted sector for data breaches, with attacks exploding over time. As per a report on healthcare breaches in the first half of 2023, 40 million Americans were impacted by 308 data breaches.
The abundant data collected, stored, and transmitted by connected medical devices has led to malicious attacks and cybersecurity breaches in medical devices. The need for proper cybersecurity protocols is critical to guaranteeing the safety and effectiveness of medical devices. Cybersecurity incidents have even resulted in the interoperability of medical devices and hospital networks, leading to potential patient harm due to delays in diagnosis and treatment.
Cybersecurity is vital to safeguarding both patients and the reputation of medical professionals and manufacturers. Therefore, organizations must ensure that medical devices are secure by addressing cybersecurity issues in medical devices, preventing potential harm to patients, and maintaining the trust of healthcare providers and the industry.
What MedTech Companies Need to Know About New FDA Guidelines on Cybersecurity?
MedTech companies must show that cybersecurity in medical devices is intact when they send them to the FDA for approval. Even though the FDA has given suggestions about security practices for quite a while, these were not mandatory until recently. But now, with the new guidance, companies have to follow these rules to ensure the safety of the people using their medical devices.
MedTech companies submitting their products for FDA approval must satisfy the following key requirements to ensure cybersecurity in medical devices: Some of the requirements are below.
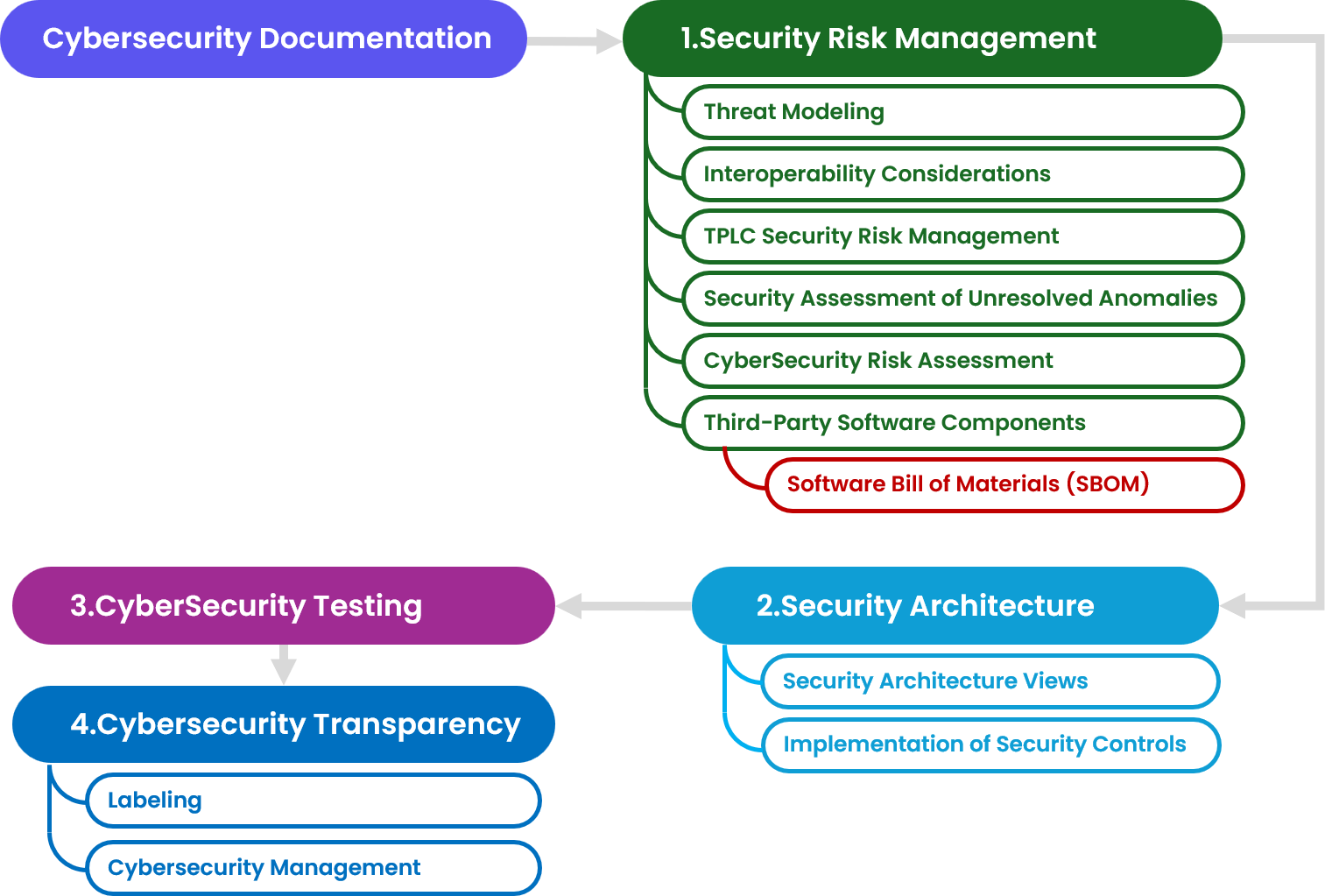
1. Security Risk Management
To ensure the cybersecurity of medical devices, manufacturers must assess the safety and security risks within the broader system in which the device operates. This involves integrated security risk management processes throughout the device's lifecycle.
Unlike safety risk management, which focuses on physical harm, security risk management deals with potential direct or indirect patient harm and other risks, including business or reputational risks.
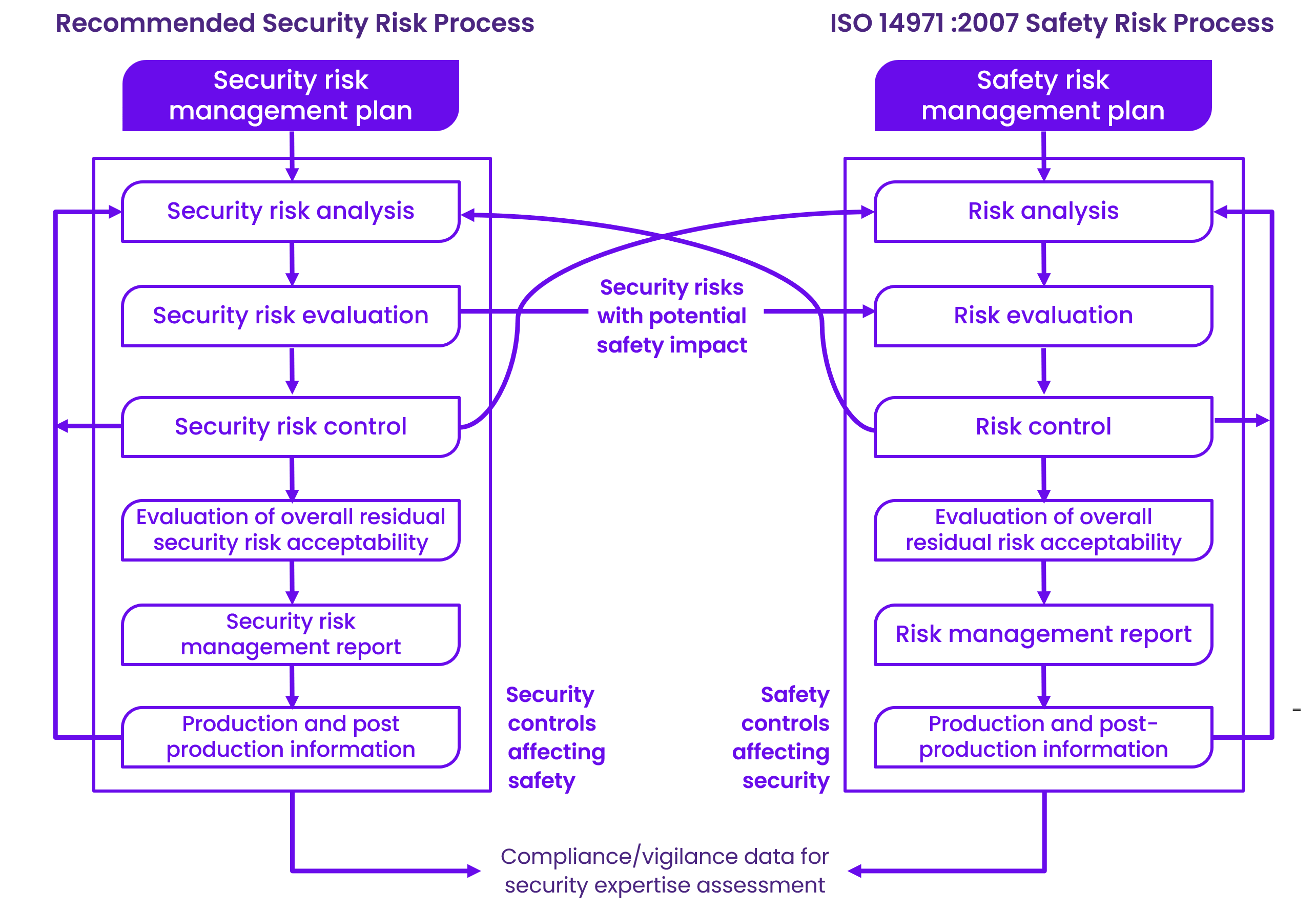
Manufacturers must design devices to eliminate or mitigate vulnerabilities; if not possible, compensating controls should be used. The remaining vulnerabilities must be documented as foreseeable risks and addressed through additional control measures or user communication.
Manufacturers need a security risk management plan, including threat modeling, cybersecurity risk assessment, Software Bill of Materials (SBOM), vulnerability assessments, and unresolved anomaly assessments. The FDA recommend to use the report described in the AAMI TIR57. This report should be part of premarket submissions, summarizing risk evaluation methods, residual risks, and mitigation activities ensuring traceability between threat models, risk assessments, SBOM, and testing documentation for a strong cybersecurity approach.
In addition, the security risk management report should:
- Summarize the risk evaluation methods and processes.
- Detail the residual risk conclusion from the security risk assessment.
- Detail the risk mitigation activities undertaken as part of a manufacturer’s risk management processes.
Provide traceability between the threat model, cybersecurity risk assessment, SBOM, and testing documentation as discussed later in this guidance as well as other relevant cybersecurity risk management documentation.
- Threat Modeling
Threat modeling is crucial in identifying security risks and vulnerabilities in medical devices. It involves defining countermeasures to prevent or mitigate threats throughout the device's life cycle. FDA recommends integrating threat modeling into the design process, addressing risks introduced through supply chains, deployment, and interoperation. Manufacturers should document threat modeling methods and rationale in premarket submissions, demonstrating how security risks impacting safety and effectiveness have been analyzed. Regular design reviews should assess device security comprehensively.
Building a threat model requires cybersecurity expertise and companies could either use experts or evaluate automated threat modeling tools that exist in the market. We recommend reviewing the MITRE threat modeling playbook for medical devices to learn how to use threat modeling in your design process.
Once the model has been created, the identification of all the possible threats can start. Those threats can be assigned to the following categories following the STRIDE model:
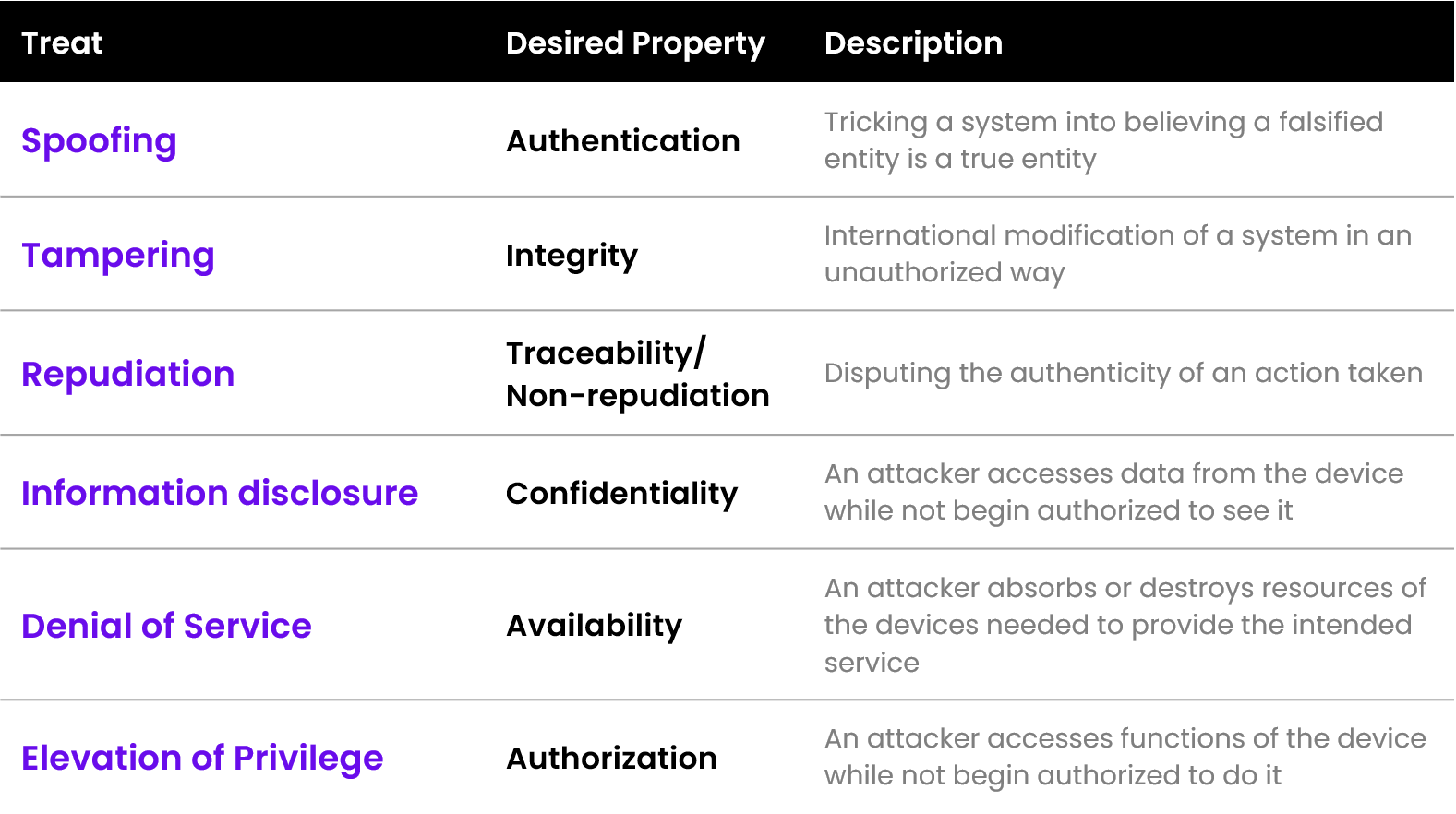
- CyberSecurity Risk Assessment
In cybersecurity risk assessment, manufacturers must evaluate security risks considering potential intentional or unintentional failures. The assessment focuses on exploitability, the vulnerability's potential exploitation.
Manufacturers should assess risks based on device and system levels, considering factors like Exploit Code Maturity and Report Confidence. Acceptance criteria should align with the device's lifecycle, addressing vulnerabilities discovered postmarket and ensuring premarket cybersecurity assessments encompass identified risks and controls from threat models.
- Interoperability Considerations
Interoperability in medical devices involves exchanging information electronically. Devices interface with medical products, healthcare systems, and computing platforms. Cybersecurity controls, while complex, ensure safe information exchange. Common protocols like Bluetooth require additional security controls for safety. Manufacturers should assess risks, follow guidance, and document cybersecurity measures for interoperability.
- Third-Party Software Components
Medical devices often integrate third-party software components, including off-the-shelf and open-source software, which introduce cybersecurity risks. MedTech companies and manufacturers must assess and document all software components, ensuring compliance with design controls and supply chain requirements.
Custodial control of the device source code is essential for ongoing risk management. Manufacturers should plan for third-party software updates and provide users with the necessary information in device labeling, emphasizing the importance of the Software Bill of Materials (SBOM) to track incorporated software.
- (a) Software Bill of Materials (SBOM) is crucial for managing cybersecurity risks. It identifies device components and vulnerabilities, aiding risk management. Regularly updated SBOMs should be part of device configuration management and included in premarket submissions for FDA assessment and user transparency in labeling.
- (b) Manufacturers must include a machine-readable Software Bill of Materials (SBOM) with specific details in premarket submissions. This includes the software support level, end-of-support date, and identified vulnerabilities. If unable to provide SBOM, a justification is needed. Manufacturers must assess and detail known vulnerabilities, their impacts, and corresponding risk controls, including compensating controls.
- Security Assessment of Unresolved Anomalies
FDA's guidance advises device manufacturers to list software anomalies in premarket submissions. Manufacturers must assess these anomalies for safety, effectiveness, and potential security implications, including Common Weakness Enumeration categories, providing clear documentation for each anomaly.
- TPLC Security Risk Management
Cybersecurity risks may continue to be identified throughout the device’s total product lifecycle (TPLC). Manufacturers must continuously assess and mitigate risks and ensure cybersecurity in medical devices is intact throughout a device's lifecycle. They should update security risk management documentation as new threats emerge, ensuring accurate risk assessment for different device configurations. FDA recommends tracking vulnerability updates, duration from identification to patching, and implementation timeframes for field devices. These metrics demonstrate effective cybersecurity compliance.
2. Security Architecture
MedTech companies and manufacturers are responsible for identifying and mitigating cybersecurity risks in their devices and associated systems, including risks introduced by network dependencies and cloud infrastructure. To address this, a detailed security architecture, defining system interactions and security measures, is crucial.
The FDA recommends including security-related design processes, requirements, and acceptance criteria within existing plans and procedures. These should holistically address device and system cybersecurity. Premarket submissions should include documentation on the security architecture, outlining system interfaces, interactions, and trust boundaries to enable FDA evaluation. Manufacturers should analyze the system environment, considering supply chain, design, production, and deployment risks.
The FDA suggests presenting this information as views, demonstrating safety and effectiveness, without creating new documents if similar details exist in other risk management documentation.
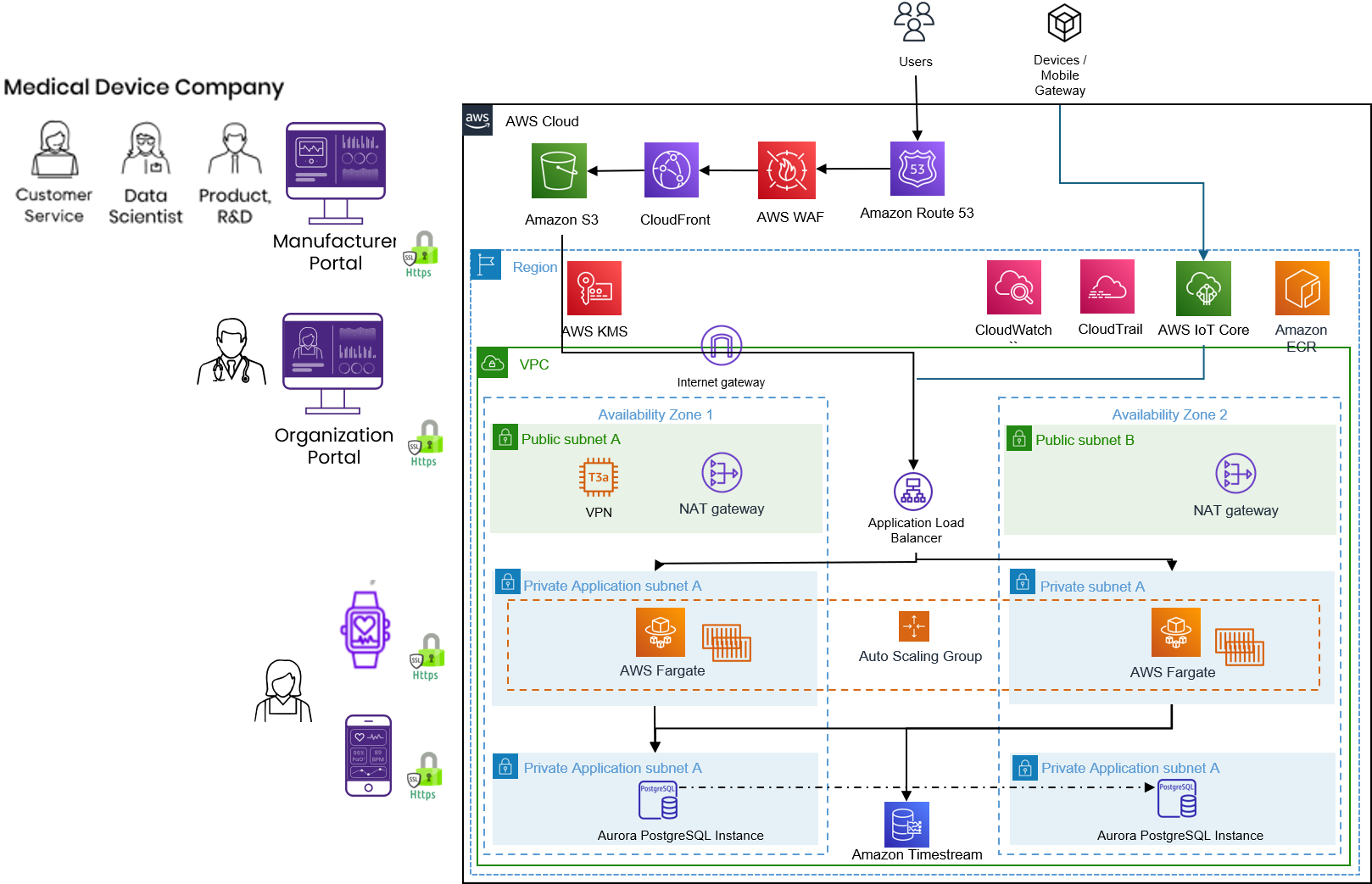
BioT’s security architecture overview
- Implementation of Security Controls
The FDA emphasizes that effective cybersecurity measures in medical devices is integrated into a device's design rather than added directly. Manufacturers must include cybersecurity controls in their design processes, ensuring they align with the device's intended use, user needs, and patient safety requirements. The FDA recommends specific security controls, including authentication, authorization, cryptography, integrity, confidentiality, event detection, resiliency, and updatability.
Manufacturers can discuss cybersecurity considerations with FDA through the Q-submission process. If using alternate controls, manufacturers must demonstrate their effectiveness and safety through detailed documentation, emphasizing the crucial integration of cybersecurity controls in medical devices early in the development phase.
- Security Architecture Views
Manufacturers are advised to create security architecture views, such as Global System, Multi-Patient Harm, Updateability/Patchability, and Security Use Case views, in premarket submissions. These views should detail system elements, interfaces, security context, and design characteristics aligned with cybersecurity objectives. Views should be tailored based on device complexity and potential risks.
(a) Global System View:
The global system view describes the overall medical device system, including the device, internal and external connections, software updates, network impact, and cloud connections. For complex systems, more detailed communication specifics can be provided in separate views.
(b) Multi-Patient Harm View:
When devices connect to other products or networks, they can pose risks to multiple patients simultaneously. In this view, manufacturers should address how their device defends against or responds to attacks that could harm multiple patients.
(c) Updatability and Patchability View:
To ensure timely and reliable updates for addressing cybersecurity risks throughout the device's lifecycle, manufacturers should provide an updatability and patchability view. This view describes the end-to-end process for delivering software updates and patches to the device, including details and considerations for non-manufacturer-controlled technologies in the update path.
(d) Security Use Case Views:
Security use cases should cover all aspects of the medical device system where a security breach could impact safety or effectiveness. These cases should consider different operational states (e.g., power on, standby) and clinical functionality states (e.g., programming, alarming, data transfer). The number of security use cases depends on the device's complexity and cybersecurity risk. Detailed information should be included in each use case, and if multiple cases share the same security assessment, diagrams and text can describe them collectively to avoid duplication.
Manufacturers aren't required to duplicate documentation if a view adequately covers identified risks, but explanations for exclusions should be provided. These views are vital to demonstrating how cybersecurity controls are integrated into the medical device system.
3. CyberSecurity Testing
Security testing is crucial for demonstrating the effectiveness of cybersecurity controls in medical devices. Manufacturers must conduct thorough testing to confirm that design outputs meet the input requirements, as per regulations. The FDA recommends including various testing types in premarket submissions, such as security requirements verification, threat mitigation testing, vulnerability testing, penetration testing, and analysis of anomalies.
Reports must detail the testing methods, scope, duration, and results. Manufacturers should assess and address vulnerabilities promptly, with plans outlined for future releases to mitigate known issues. Cybersecurity testing should be conducted throughout the development and post-release phases, ensuring continuous assessment of potential vulnerabilities and timely responses to prevent exploitation. Early testing prevents delays in release timelines and costly redesigns, while regular post-release testing ensures ongoing device security and effectiveness.
Summing Up
Incorporating the FDA's recommended cybersecurity measures into medical devices is essential for ensuring their safety, effectiveness, and competitive edge. By adhering to these guidelines, MedTech companies and manufacturers can enhance their products' resilience against potential threats. For personalized advice on implementing FDA-recommended cybersecurity practices, please feel free to contact us at BioT-Medical via email at info@biot-med.com or call us at: +972-74-7024735.
Stay ahead, stay secure, and innovate responsibly.

